In the world of cybercrime, targeting of businesses is commonplace.
It is not just large businesses that are threatened by such attacks. Unfortunately, whether an organisation is big or small, the vulnerability exists. And it is important to be cognizant of disruptions that such attacks can bring about.
This is certainly an important topic for both—your enterprise cloud phone system as well as your overall business.
Read on as you build your strategy against DDoS attacks.
What is a DDoS attack and what are its symptoms?
DDoS stands for Distributed Denial of Service. In simpler terms, DDoS refers to a digital attack that renders a service unavailable for users.
In cyberattacks, this happens when a system on the Internet begins to send a targeted overload of requests or malware to a web server.
When such malware or malicious requests come in from multiple systems connected on the Internet, we call it Distributed Denial of Service or DDoS.
The modus operandi of attackers is simple—swarm a web server with an extraordinarily large number of requests for a page or a barrage of queries to a database.
In both cases, attackers choke either the bandwidth or resources of the web server like CPU or the available RAM.
Invariably, there are initial symptoms such as a possible break in the network or just a server going down. Only an analysis of the traffic gives real insights into the severity of the attack.
Now, the drop in services can happen due to the unavailability of either or some of the following:
- Servers
- Attached devices
- Applications
- Networks
- Certain types of transactions in applications
When a web server comes under such an attack, the disturbance may range from a denial of service for a short period of time to something as severe as the whole system crashing.
Types of DDoS attacks
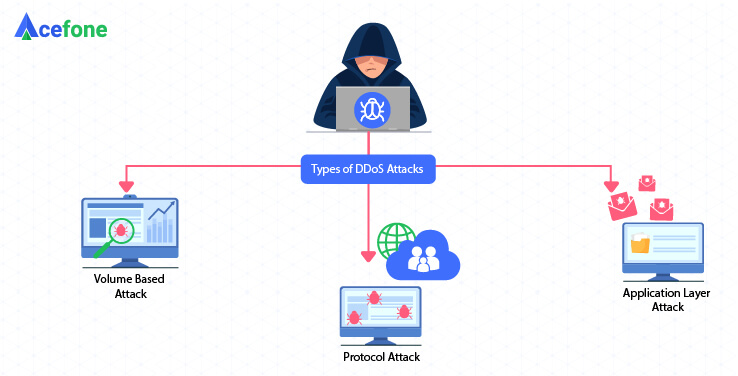
While such attacks can come camouflaged in a multitude of ways, they all have the same underlying objective—to choke the resources to a point where access becomes extremely slow or completely unavailable.
These attacks can broadly be classified into three key types:
-
Volume attacks
Measured in bits per second, or BPS, such attacks happen through huge volumes of malicious traffic targeting a web server or a particular website
-
Attacks on network layer
Network layer attacks are measured in packets per second or PPS. They involve an extraordinarily large number of packets sent to the targeted infrastructure. The points of such attacks are the network management tools and/or the network infrastructure itself
-
Attacks on application layer
Measured in requests per second, or RPS, these attacks are created with malicious intent and send a flood of requests targeting a specific application
Key tips for mitigating DDoS attacks
DDoS attacks have been around for almost two decades now and have evolved over time. They are now sharper, more incisive and, as we have seen, come in different forms.
Let us review some tips that will help you minimise the impact of such attacks. These are relevant for all aspects of your business, starting with your cloud system.
-
Plan ahead
From the different types of attacks listed above, we know that primary vulnerabilities show up in the network infrastructure, connected devices, and applications.
This step is all about accepting the fact that an attack is inevitable, sooner or later. And thus, planning a suitable response in advance.
In other words, the first step, and possibly the most important one, is to create a plan that an organisation can put into action almost immediately to fight the attack.
Such plans are usually referred to as emergency responses. One should identify points of vulnerability in all three components, seek expert advice and document the plan during the initial set-up itself.
Following need to be part of the plan for appropriate mitigation:
- A disaster recovery plan (DRP) including fail-over networks in case the DDoS attack actually takes over the entire system
- Infrastructure diversity—both in the type of components used in infrastructure and their geographical deployment
- Using a combination of private and public cloud systems
- For enterprises, it makes sense to integrate their network and application teams for a cohesive plan, with suitable escalation mechanisms that kick in when the attack actually occurs
An effective way that is used by enterprises is to have a larger number of wide-area network (WAN) entry points. They also enlist cloud scrubbing service providers in order to re-route such attacks to scrubbers.
We will talk about such service providers further in the article.
-
Refinements and adjustments
Attackers with obvious malicious intent are getting smarter and more innovative. They are now able to modify attacks based on the responses of companies.
In real-time, they are able to attack from a different IP, a different port, or even a different protocol. It is thus important to continuously adjust and refine the response to such attacks.
-
Agreements with mitigation and protection service providers
There is a lot that companies can do themselves to establish an operational response plan. However, to augment their efforts, it is advisable to take help from service providers in this domain.
On one hand, a business gets the benefit of advice from domain experts; their services are also more affordable than putting it all together. Leading platforms that specialise in filtering malicious traffic, such as the cloud-based DDoS mitigation platform, can absorb volumetric surges before they ever reach your network. The other benefit is that these service providers also collaborate within themselves and are, thus, ahead on the knowledge curve.
Even if you’re signing up for external service providers, you can still monitor everything in-house to ensure alertness in case of abnormal traffic.
-
Onsite devices are never enough
However powerful or secure onsite devices like firewalls, load balancers or even systems for prevention of intrusion may be, the fact is that they may not be able to block off all types of attacks.
While these tools are extremely crucial in setting up defensive measures, there are certain inherent vulnerabilities that attackers can target despite these protections.
The key here is to handle such attacks before they land on your on-site devices. Services offered by third party providers come in handy while diverting the attacks away from the main site.
-
On-site actions for application layer
For the application layer, network mitigations may not be successful as targeted attacks on certain applications can still go through on-site protection devices.
For these applications, you will need tools for web protection in your data center.
Such tools enable you to conduct deep inspections at packet levels to view the application layer. These are possibly the best mitigation tips for attacks on individual applications.
Another approach is to deploy application redundancy through multiple cloud systems. This way, in the event of an attack on the application, you can always switch to another cloud network.
-
Collaborate
It will be helpful to share information and mitigation plans with companies in the same industry or domain.
Collaboration on a topic like this, with mutual sharing of knowledge and information, will be immensely helpful to all participants. Your telecom service providers are the other party that you can collaborate with as you plan and refine your responses to DDoS attacks.
-
Remain vigilant, especially for secondary attacks
Another trend that is becoming more common is a more targeted or sustained attack following an initial DDoS attack. In other words, the first attack may just be a distraction to something bigger.
DDoS attacks may just be deployed to create a panic situation, while a backdoor application gets targeted to extract more valuable data.
Conclusion
Attackers do not just target large enterprises. They can target all types of businesses, whether large or small.
Your cloud phone system, or even upstream providers like telecom, are equally vulnerable. In certain instances, attackers have also taken an indirect route to target a particular company’s information.
We have reviewed the different types of attacks and how they may be multi-pronged, increasing the scale of their impact.
Planning for mitigation is simpler than it may seem. There are domain experts that can offer invaluable advice to keep you and your data secure.
The bottom line is to plan, review, refine, and evolve. And this needs to keep pace with the evolution of sophisticated attackers.
If you are looking to implement secure cloud communications for your business, then connect today with our cloud experts at 1888-859-0450 or write to us at [email protected]